I regularly talk about the history and direction of enterprise mobility with my customers and colleagues, so i thought I’d try and pull a few of those thoughts together. It’s been an interesting journey so far. The way in which enterprises enable their employees to use mobile devices has changed immensely over the last 15 years, and the direction of travel is becoming pretty exciting! (Well, at least I think so!).
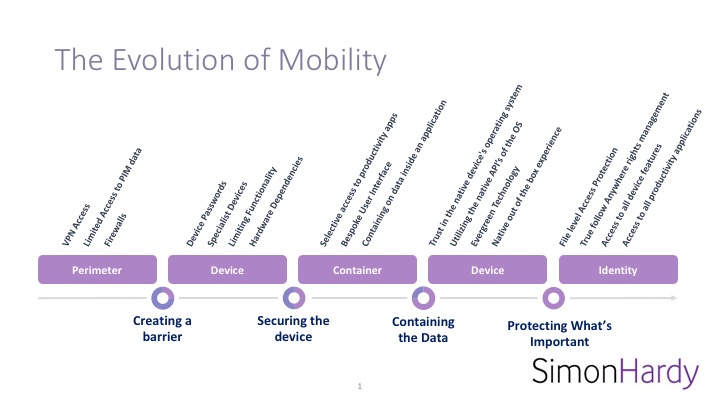
In the beginning… (Couldn’t resist), we came from a world where everything was kept behind the perimeter of the corporate network (still are in many cases). Access with mobile devices was limited to those that could dial in via a VPN, and even then that was limited to PIM data only. There was nothing standard, and only a few mobile devices out there that offered anything like mobile email.
The First Fruit…
Then, along comes the BlackBerry. A specialist device, with a specialist matching BlackBerry server sitting behind the perimeter of the corporate network, with all data traveling across a special network to keep your data safe through the entire journey. These devices were provided by your office, and they were fantastic business tools. if configured correctly, not only did you have access to your email, calendar and contacts, you could also book meeting rooms, access your files on the network, IM and so much more.
A New kind of Fruit!
Then, something happened (10 years ago this month), the iPhone was released. Now, it took a few years to make it to the enterprise, but when it did it created a massive headache for IT and corporate security teams across the globe. Execs and senior leaders in these companies wanted to use these new expensive devices, but there was no truly secure or simple way to do this. The devices weren’t secure, they connected via ActiveSync (well, not even the first iPhone did that!) and we didn’t trust them, there was no remote way to ensure security on them, no proper encryption, and no way to get corporate data from the network, onto the device in a way that ticked all the boxed for both security and for a good user experience.
Containerisation…
Here is the point in history when we saw the rise of the software container. A special application that you would install on your device, where all your corporate data is held, be it emails and calendars, or documents and files. It did (normally) require a specialist server behind your corporate network again, and the data traveled over a secure connection. This app was secure enough that we didn’t have to worry about the levels of security on the device as we knew the data was secure. The biggest problem though, was user experience. It was poor. Wasn’t on par with the native user experience of the new mobile devices out there, and the limitations around notifications and the constant battle between the device and platform developers was never ending.
In devices we trust…
Luckily though, this was only the prime option for a few years. Here is where we make the move back to trusting the device again. At first with iOS, and now with Android and their Android for Work capability, we’re seeing better developed security and enterprise capabilities that allow us to use the built in functionality to better maximise the user experience and still keep control over the corporate data in a balance way.
Identity is the new security
Now, we’re entering into an interesting area of mobile access to enterprise data. We’re are in the era of identity. This is where rather than securing our data by placing it in a secured application, or by making sure the device it’s self is secure, we secure the documents and data it’s self. By securing the documents, and determining who has access to these documents you are negating the need to put them somewhere safe. They can be stored on any device, on any platform, and as long as the user can be authenticated they can safely access without trouble.
Where we go next.. Well that’s another question entirely, but identity is going to keep mobility busy for a few more years yet!
